
The Adani group was hit by allegations of serious fraud and account manipulation on 24th January 2023.
The
international research group that investigates such frauds and goes
short on companies that are perpetrating such frauds released a report
and went short on Adani shares.
They
predicted an 87% downside to the Adani shares and their word came
almost true. Many of the Adani Group companies valuations fell between
50% to 85% before knights in shining armor, like the LIC and SBI came
for the resuce, both prompted by the Government of India, led by
Narendra Modi.
As
is the pattern adopted by Narendra Modi and his colleagues, they went
in to damage control. To do this, they somehow got the Supreme Court to
take suo-moto cognizance of this fall in share prices. The SC has no
business to take such notices as there is an independent authority, the
SEBI, which is the market regulator. The SC, led by DY Chandrachud,
decided in its own wisdom to come to the ‘rescue’ of Indian Investors.
It is pertinent to note that almost 75% to 85% shares were held by Adani
and his front companies. So, the biggest impact was on Adani.
This
is the Modus Operandi of Narendra Modi Government. When ever it is
faced with a problem, it gets the SC to intervene. It did this during
the controversy that erupted in the Judge Loya case, it did this in the
Zakia Jafri review petition and it did this in the case of crash of
Adani Shares. What it does is that it gets the SC to institute an
inquiry into the case and then manages to get a favorable verdict. In
the Judge Loya case, then CJI Dipak Misra, took over all cases filed
anywhere in the country and decided to hear the case himself. He later
accepted the oral testimony of four judges who were present with Judge
Loya on the night of his death and disregarded all other information
that was available in public domain.
In
the Adani case too, the SC appointed a six member investigation team,
comprising of a retired judge and five prominent businessmen.
This
inquiry returned a clean chit for Adani. SEBI, which was also part of
the case, then issued a clean chit on its own and said that Adani had
not done anything wrong.
It would be interesting to get the transcripts and details of both these investigations.
As
Adani had accessed funds from the US Stock Markets, the SEC (Securities
and Exchange Commission) started a parallel investigation based on the
allegations of Hindenburg Research’s report.
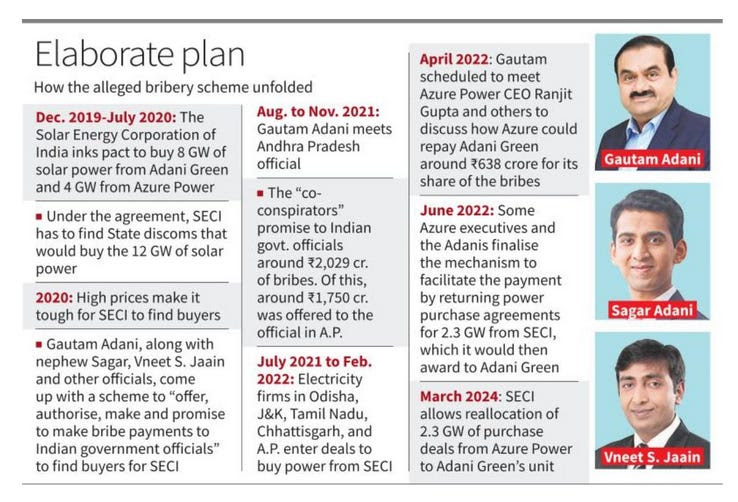
Along
with FBI, it raided the director of Adani Green Energy, Sagar Adani,
the nephew of Gautam Adani and confiscated damning evidence that
suggested that the company that had raised money in the US had paid
almost 250 Million US Dollars to government officials in India as bribes
for getting Power Purchase Agreements signed. These PPA would have
given the group bumper profits of 2 Billion USD over the agreement
period.
The
four governments named are the Government of Andhra Pradesh, then led
by Jagan Mohan Reddy of YRS Congress, Government of Odisha, then led by
Naveen Patnaik, the Government of Tamil Nadu, led by DMK, the Government
of Chattisgarh, led by Bhupen Bhagel of Congress and J&K, led by
the Governor, who was an appointee of the BJP.
In a press conference, Sambit Patra, the BJP Spokesperson pointed this out and said that no BJP State Government was paid.
What
people need to understand is that when Adani is Modi’s man and when no
CM in any BJP ruled state is an independent CM, all are puppets of Modi,
there was no need to pay anyone in those states. The money would have
been already paid to BJP anyway.
The
US Department of Justice has now indicted seven people, including
Gautam Adani and Sagar Adani and issued arrest warrants for all of them.
If prosecuted, everyone faces a 20 year jail term for wire fraud and
corruption charges.
There
is an option available for the Adani group to accept the wrong doing
and settle the mater with SEC. Many companies have done this in the
past. I am sure that Adani will take that route rather than face jail.
The SEC will impose penalties and give guidelines that can’t be
violated. The amount of penalty is usually made public.
If Adani takes that route, then one thing will become clear, that he has accepted his guilt.
What
the US DOJ investigation done along with FBI shows is that the
investigation done in India was a sham. That the special team was
completely compromised, that the SEBI, led by Madhabi Puri Buch was
totally compromised and the SC accepted the reports at face value, thus
it can’t escape blame for allowing such a fraud from going undetected.
This is the tale of two investigations, one done as a sham and the other done diligently.
The
members of the expert committee included former chairman of the State
Bank of India O.P. Bhatt, retired Bombay High Court judge Justice J.P.
Devadhar, former chief of the New Development Bank of BRIC countries
K.V. Kamath, co-founder of Infosys Nandan Nilekani and securities expert
and lawyer Somasekhar Sundaresan.
The
members of this expert committee should be questioned as to why they
were not able to find anything amiss? Madhabi Puri Buch needs to be
sacked right away and the records of SEBI investigation should be sought
and made public.
Finally,
this is another blot of the legacy of former CJI D.Y. Chandrachaud. Not
the first, neither the last. As time goes by, more such blots will
appear on his legacy.



:max_bytes(150000):strip_icc()/money-laudering-6cb10f0b844d460a99ab04b349da29ae.png)





